The general trend of malware implemented in Java programming language is increasing. Thanks to Java’s platform independent bytecode technology and the wonderful VirtualMachine.
Analysis of Java bytecodes is relatively simple task (unless it is obfuscated). There has been some very nice tools to decompile the bytecode back to source with great accuracy.
For a change, in this blog post, I have chosen to write about the dynamic analysis of a Java Applet. The entire analysis is carried out inside a controlled (simulated) networking environment using Zelster’s Remnux VMImage as the internet server.
Payload of OpenConnection:
- As the name suggests, the Applet accepts a parameter named “URL”.
- It opens a URL connection with the URL (typically an executable file).
- It reads the binary data from the Socket’s input stream and writes it to a File object’s OutputStream (in %temp% folder).
- Once, the file is successfully downloaded, it spawns the downloaded executable.
Ok, the payload is very familiar one and nothing exciting about it. Lets see the dynamic analysis steps:
Step 1: Decompile the class file. There has been many decompilers available. [I personally use jad or jd-gui]
Step 2: Include some debug statements (some System.out.println statements here and there to print value of the variables )
Step 3: Compile the file to create the class file and pack it as a jar archive.
Step 4: Now, to satisfy the Java security model, an Applet has to be signed to access local file system and do process related activities. We use JDK’s keytool and jarsigner for this step.
Step 5: now the jar file is signed, we will host this jar file along and a companion html file to the Remnux server.
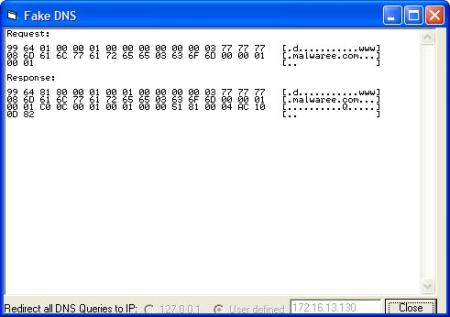
Step 6: Now start the FakeDNS.exe in the test machine and resolve all the domain queries to the Remnux server.
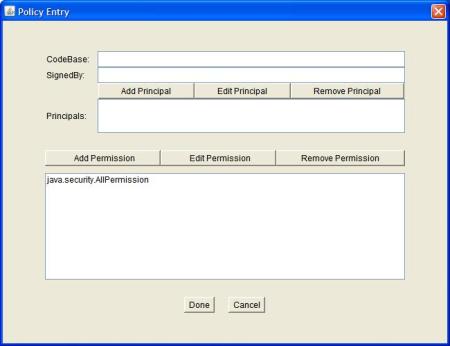
Step 6: To create a perfect ecosystem for the malware to flourish without any obstacle, we need to lower the Java’s default sandboxing security policy. This can be done by JDK’s policytool.exe
Step 7: With everything set, access the html file hosted in the remnux server that embeds applet into it.
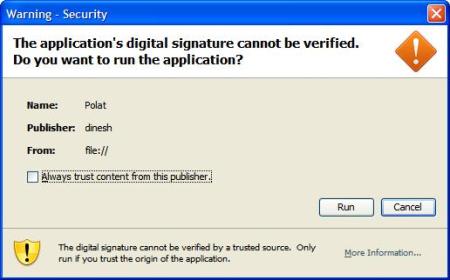
Step 8: The user is presented with a warning about the active content about to be executed and asks your approval to trust the self signed certificate.
Step 9:Now, the init() method of the applet is called, which inturn invokes the method that opens a connection to an executable (again hosted in remnux server. in this example, i have hosted winmine.exe)
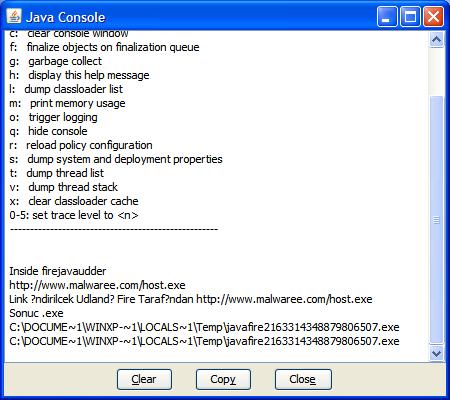
Step 10: The debug messages can be seen in Java Console.
Step 11: Once the sample is downloaded, it spawns the executable. (in this case winmine.exe). The Parent-child relationship can be seen through process explorer.
This stresses the importance of paying attention to the security popups even during a casual browsing session.
Cheers 🙂